這兩天做LAB發現ASA詭異的行為,下圖為架構。
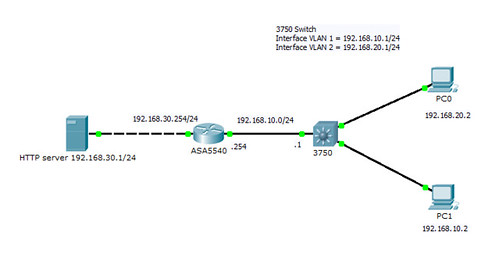
IP與MAC對照表
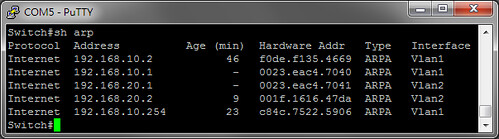
PC0向ASA後方的http server發出一個TCP SYN,但source IP偽裝成PC1(192.168.10.2)。
用ASA packet capture來抓包:http server乖乖的回應了一個SYN ACK。

從PC1來抓包,的確收到server送來的SYN ACK,並且如預期中由ASA直接丟過來。
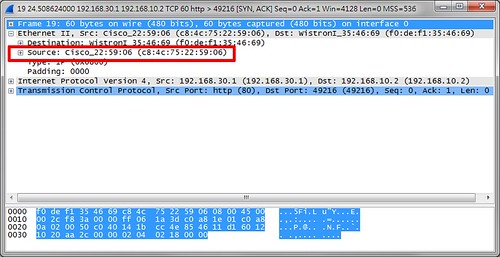
OK,後面開始進入重點。
PC0向ASA後方的http server發出一個TCP ACK(注意,是ACK),同樣的,source IP偽裝成PC1(192.168.10.2)。
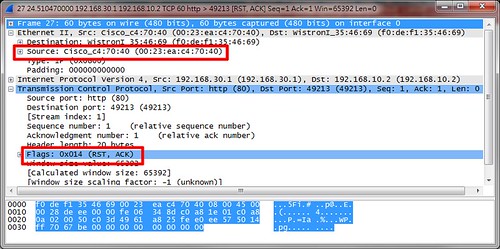
ASA發現這條connection沒有SYN,所以就把收到的ACK給GG了,此外他還回送一個TCP RESET來終止。
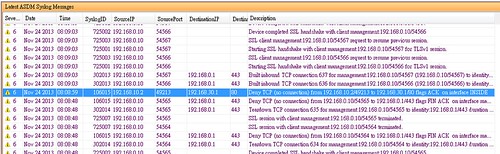
問題就在這個TCP RESET上。請注意dest MAC,ASA是轉送給192.168.10.1,而不是直接丟給192.168.10.2,即便他們就在同一個網段。(下圖為ASA packet capture抓包)

(用PC1抓包)證實這個包先到了192.168.10.1再到PC1。即使在ASA寫一條static ARP來對應PC1也不會改變ASA的繞送行為。
是甚麼機制或是設計考量讓ASA會有這樣的行為,我目前也還在找答案,還請各位大德不吝賜教。
附上ASA和switch的config。
running-config of 3750-48TS
version 12.2
no service pad
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname Switch
!
boot-start-marker
boot-end-marker
!
!
no aaa new-model
switch 1 provision ws-c3750-48ts
system mtu routing 1500
ip routing
!
!
spanning-tree mode pvst
spanning-tree extend system-id
!
vlan internal allocation policy ascending
!
!
interface FastEthernet1/0/1
switchport mode access
spanning-tree portfast
!
interface FastEthernet1/0/2
switchport mode access
spanning-tree portfast
!
interface FastEthernet1/0/3
switchport access vlan 2
switchport mode access
spanning-tree portfast
interface Vlan1
ip address 192.168.10.1 255.255.255.0
!
interface Vlan2
ip address 192.168.20.1 255.255.255.0
!
ip classless
ip route 0.0.0.0 0.0.0.0 192.168.10.254
ip http server
ip http secure-server
!
!
no cdp run
no cdp tlv location
no cdp tlv app
!
!
line con 0
line vty 5 15
!
end
running-config of ASA
ASA Version 9.1(3)
!
hostname ciscoasa
enable password 2KFQnbNIdI.2KYOU encrypted
xlate per-session deny tcp any4 any4
xlate per-session deny tcp any4 any6
xlate per-session deny tcp any6 any4
xlate per-session deny tcp any6 any6
xlate per-session deny udp any4 any4 eq domain
xlate per-session deny udp any4 any6 eq domain
xlate per-session deny udp any6 any4 eq domain
xlate per-session deny udp any6 any6 eq domain
passwd 2KFQnbNIdI.2KYOU encrypted
names
!
interface GigabitEthernet0/0
nameif INSIDE
security-level 100
ip address 192.168.10.254 255.255.255.0
!
interface GigabitEthernet0/1
nameif OUTSIDE
security-level 0
ip address 192.168.30.254 255.255.255.0
!
interface GigabitEthernet0/2
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet0/3
shutdown
no nameif
no security-level
no ip address
!
interface Management0/0
management-only
nameif management
security-level 100
ip address 192.168.0.1 255.255.255.0
!
ftp mode passive
access-list PERMIT_OUTSIDE extended permit ip any4 any4
access-list PERMIT_ICMP extended permit icmp any4 any4
pager lines 24
logging enable
logging asdm informational
mtu management 1500
mtu INSIDE 1500
mtu OUTSIDE 1500
no failover
icmp unreachable rate-limit 1 burst-size 1
asdm image disk0:/asdm-714.bin
no asdm history enable
arp INSIDE 192.168.10.2 f0de.f135.4669
arp timeout 14400
no arp permit-nonconnected
access-group PERMIT_OUTSIDE in interface OUTSIDE
route OUTSIDE 0.0.0.0 0.0.0.0 192.168.30.2 1
route INSIDE 192.168.20.0 255.255.255.0 192.168.10.1 1
timeout xlate 3:00:00
timeout pat-xlate 0:00:30
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
dynamic-access-policy-record DfltAccessPolicy
user-identity default-domain LOCAL
aaa authentication ssh console LOCAL
http server enable
http server idle-timeout 180
http 192.168.0.0 255.255.255.0 management
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart
crypto ipsec security-association pmtu-aging infinite
crypto ca trustpool policy
telnet 192.168.0.0 255.255.255.0 management
telnet timeout 5
ssh 192.168.0.0 255.255.255.0 management
ssh timeout 60
ssh key-exchange group dh-group1-sha1
console timeout 0
dhcpd address 192.168.0.2-192.168.0.254 management
dhcpd enable management
!
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
username cisco password 3USUcOPFUiMCO4Jk encrypted privilege 15
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect ip-options
inspect icmp
!
service-policy global_policy global
prompt hostname context
no call-home reporting anonymous
call-home
profile CiscoTAC-1
no active
destination address http https://tools.cisco.com/its/service/oddce/services/DDCEService
destination address email callhome@cisco.com
destination transport-method http
subscribe-to-alert-group diagnostic
subscribe-to-alert-group environment
subscribe-to-alert-group inventory periodic monthly
subscribe-to-alert-group configuration periodic monthly
subscribe-to-alert-group telemetry periodic daily
: end
沒有留言:
張貼留言